Opinion
U.S.A. –-(Ammoland.com)-In part 2 of AmmoLand’s guide to Privacy, we took a look at VPNs, DNS servers, and password managers. In this part of the guide we will be discussing how to protect your privacy on your computer and your internet-enabled devices. Although these techniques will not keep you totally safe, they do go a long way in protecting your privacy.
What most people do not know is that every time you go to a website your device downloads all text and pictures on the site. When you close your browser, your device does not delete these pictures. They are still in your temporary files. If you accidentally go to a website with illegal content it is still on your computer when you leave the site.
Also, your browser stores your internet browsing history. Anyone that gets access to your device can see everything that you did online. The courts have used this information against people.
In this era of thought police, we need to be vigilant. A lot of people surf the Internet from work computers and legal guns are frowned upon by a lot of employers.
Another thing that happens when you go to a website is that the web server places a small piece of data on your device. This short text string is called a “cookie”. Sometimes cookies get a bad rap, but for the most part, they are helpful.
Understanding Cookies
Cookies store things like session IDs. When you sign into a website a lot of times, you will not have to sign in again when you go back to the site. This convenience is accomplished by the session id that the site generates and places on your computer and the web server. Cookies can also store other information to do things like autofill out forms.
Although cookies are not necessarily bad, anyone who gets access to your device can use tools to extract information from these cookies. Luckily for us, there is an easy way to prevent our device from storing this information. Although it might be overkill on your home devices, it is critical on shared devices such as library computers. When I spent time in eastern Europe the hotels didn’t have WiFi, but they did have shared computers for guest to access the Internet.
Incognito Mode
The way we prevent our devices from storing this information is to used modes known as private browsing. In Chrome, this mode is called “Incognito” mode, in Firefox it is called “Private” mode, and in Microsoft Edge, it is called “InPrivate” browsing. Every browser will have a private browsing mode.
When using these modes once you close your browser, it will delete all the stored information currently on your computer. Although this doesn’t keep us completely safe, it does help a lot. In InfoSec (info security) it is about using multiple techniques to mitigate risk, and this should be the starting point.
Encryption
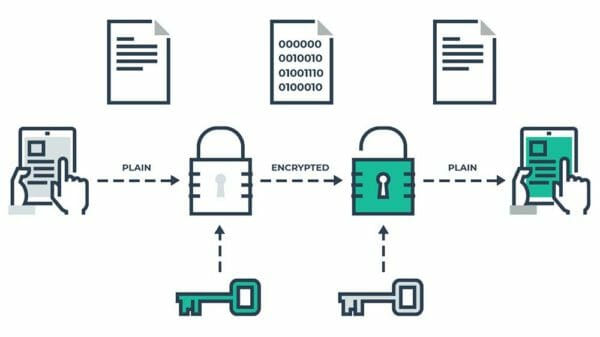
One of the most important things we can do to protect our data on our devices is to use encryption to prevent unauthorized access. What encryption does is encodes your data so that no one can access it without a passcode. Users can use this safety measure on all forms of devices such as phone, tablets, and computers.
Contrary to the movies, encryption is not easy to break. To break encryption in the real world, it takes years and supercomputers. Most hackers will look for a way around encryption instead of trying to break the encryption itself. That is why the International Traffic in Arms Regulations (ITAR) regulates the export of encryption, and some countries outright ban it.
Most devices have an encryption option built into the operating systems. Mobile devices are the most important things to encrypt because these devices are the easiest to lose since we take our phones everywhere with us. Just think how much information you store on your phones, and what people could do with that information.
Turning on Encryption in Andriod Devices:
- Go to the Apps Screen.
- Tap the Settings icon.
- Scroll down until you see the Security icon.
- Tap Encrypt Device
- On the next screen tap the Encrypt device button at the bottom of the screen
Turning on Encryption in IOS:
- Tap the Settings app.
- Tap Touch ID & Passcode.
- Tap Turn Passcode On.
- Enter a Passcode
Turning on Encryption in MacOS (FileVault):
- Click on the Apple menu and select System Preferences.
- Select Privacy & Security.
- Click on the FileVault tab, then click the lock in the bottom left corner of the window.
- Enter your administrator name and password and click Unlock.
- Click Turn On FileVault.
- Choose whether you want to link your iCloud account to FileVault to unlock the disk and reset your password or create a recovery key and click Continue.
- Click Restart to reboot your Mac and begin the encryption process.
Due to the multiple steps and checks required to turn on encryption in Windows 10 (BitLocker), please follow this guide: www.windowscentral.com/how-use-bitlocker-encryption-windows-10
The drawback to encryption is that it slows down drives, but since the rise in use of high-speed hard drives such as solid-state drives this drawback is mostly mitigated by technology. I encrypt everything and do tons of video editing, and I have never had any issues with speeds.
Virus Protection

Now we need to talk about Virus protection. No matter if you have a Windows PC, Mac, or only a mobile device you need virus protection. Viruses are more dangerous than ever. They are more advanced and more damaging.
What most people call viruses is malware. Viruses are just one type of malware. Other types of malware you might have knowledge of are trojan horses and internet worms. All we need to know for this article is these things are bad for your devices and what we call anti-virus software is really anti-malware since it protects against all of the above types of malware.
Malware of the past were works of bored kids in their bedrooms who got their kicks by causing grief for unsuspecting computer users. These types of malware are almost all extinct. Devices are more hardened than they were 10 to 20 years ago, but the current malware is generations more advanced as well.
Most malware falls into two categories. The first is malware for the financial gain of the creator. Ransomware is an excellent example of this type of malware. The “Wannacry” ransomware would encrypt your drives and will not decrypt until you paid the hackers for the key. Many people and even hospitals paid the ransom. Luckily, someone found the kill switch that stopped the spread of the ransomware.
The second type of malware is even scarier than the first. This type is state-sponsored malware. The Stuxnet worm is an excellent example of this type of malware. It is believed to have been developed by a partnership between Israel and the US. The worm wreaked havoc on the Iranian Nuclear program bringing it to its knees. Almost all countries have some form of a cyber warfare program.
If you work for a government alphabet agency, then you have a big target on your back when it comes to state-sponsored malware. This targeting is why malware protection is so important to have on all our devices no matter if it is a computer or mobile phone.
The best anti-virus program for Windows or MacOS is Bitdefender Antivirus Plus. Almost all internet security experts recommend Bitdefender or Kaspersky Anti-Virus. I stay away from Kaspersky since it is a Russian company. A Chinese mobile phone company was recently caught leaking user information to the Chinese government. I can see a Russian company helping the Russian government in the same way.
For Android devices, the best pure anti-virus is Avast Mobile Security although Bitdefender comes in a close second. I still would go with Bitdefender since it has built adware protection in addition to the anti-virus protection. It also has a built-in VPN, but it is slow so I wouldn’t use it. It will work in a pinch for light web surfing or email.
For Apple mobile devices I like McAfee Mobile Security. Its virus protection is top notch. One of the cool things that it does is if your phone gets stolen you can remotely have the camera take a picture of the person with the phone. It will also give you a GPS location so you can track down the thief.
Spyware
Spyware is another huge problem. Spyware is a generic term that means any program that hides on your computer and monitors what you do. The program then sends information back to a server that is run by the spyware developer.
Spyware is prevalent on the internet. Most of the time sites trick the user into downloading spyware by having the user click on a pop up that says something like “Your Flash player is out of date. Click on a link to download a new copy.” You should never click on or open these links!
Other than just spying on you the software can slow down your computer by a significant margin since all data is sent to a remote server that usually located in a foreign country. If you notice your computer or device slowing down, it might be time to scan for spyware.
The best anti-spyware software for any platform is Malwarebytes. There is a free version and a premium version of the software. I highly recommend the premium version of Malwarebytes. It gives you overall better protection and protects against ransomware. It also has great phishing (attempting to trick the user into giving up their information) protection.
These are just a few steps to help you stay safe on the Internet. Remember, there is no silver bullet in online safety. In part four we will go into some alternatives to popular websites. These alternatives value your privacy.

About John Crump
John is a NRA instructor and a constitutional activist. He is the former CEO of Veritas Firearms, LLC and is the co-host of The Patriot News Podcast which can be found at www.blogtalkradio.com/patriotnews. John has written extensively on the patriot movement including 3%’ers, Oath Keepers, and Militias. In addition to the Patriot movement, John has written about firearms, interviewed people of all walks of life, and on the Constitution. John lives in Northern Virginia with his wife and sons and is currently working on a book on leftist deplatforming methods and can be followed on Twitter at @crumpyss, on Facebook at realjohncrump, or at www.crumpy.com.






John, Good start. 1) I was hoping for more information (hopefully in the future) about VPNs. 2) I would also suggest a password manager (the real reason for my comment). Personally I use 1Password which: a) allows me to store the passwords in an encrypted vault both on my machine and in their cloud. b) warns me of passwords I have used in more than one place (this is a generally poor practice) c) warns me of websites that have been compromised where my password may be in danger d) warns me of websites that do not have secure connections… Read more »